Curious about the advantages of AI in cybersecurity? Explore how AI enhances threat detection, fortifies defenses, and streamlines incident response for robust digital security. The digital age is changing our…
Welcome to our blog, where we will be exploring cybersecurity control – a topic that should attract your attention since more and more cyber threats are arising. Cybersecurity control is…
How To Build A Secure Mobile App 10 Tips! Every passing year since the last two decades, the use of mobile apps is grown exponentially. Today, there are more internet-connected…
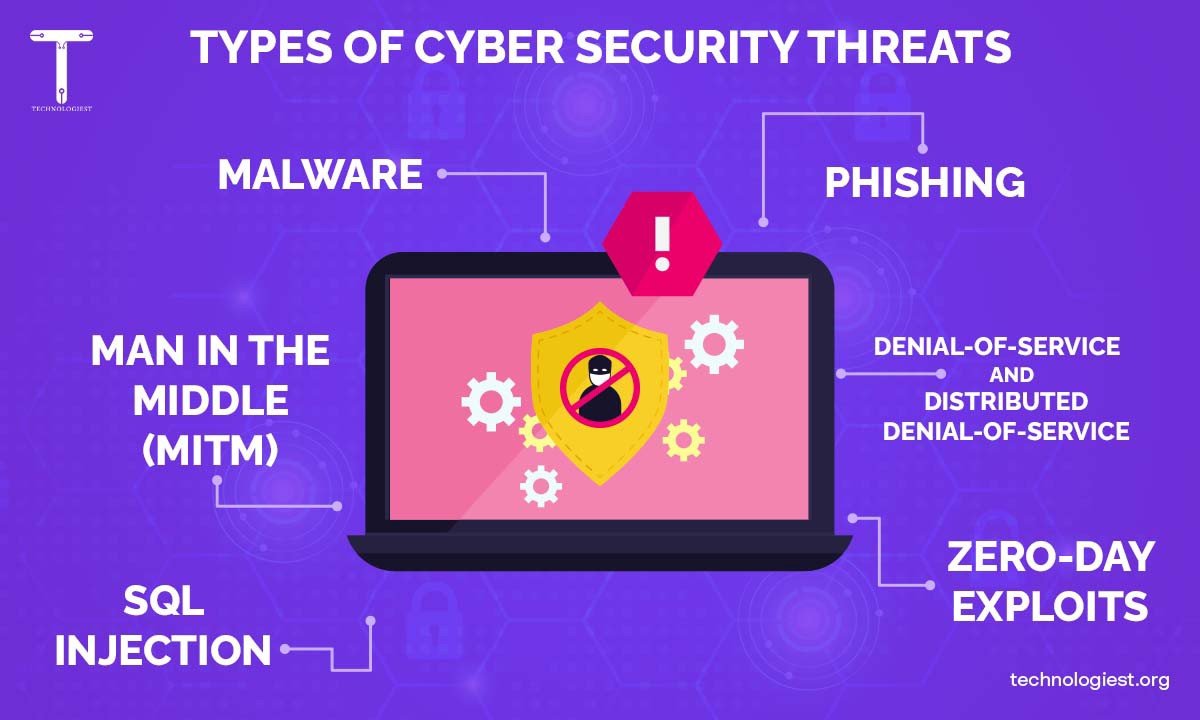
In times like these, we are always open to different types of cyber security threats. The nature of these threats is rapidly changing as we sink deeper into the digital…
Knowing cybersecurity basics is important for safeguarding your networks and devices from any acts of assaults, damage, or sabotage as well as unauthorized access. It works as the last line…
Organizations face a constantly changing range of risks in the fast-paced field of cyber security, from cunning insider assaults to highly skilled foreign hackers. Although external threats frequently make the…
In an era of widespread data sharing and digital connectivity, the privacy of personal information is in danger. Social security identity theft sticks out in this context as a horrifying…
Nowadays, with almost every part of our lives being online, protecting our online identity has become crucial in this digital age. Cybercriminals often compromise our virtual identities by obtaining financial…
An essential step in the fields of research and information technology is data collecting. It entails obtaining information from a variety of sources in order to analyze and understand it….
In recent years, the surge in popularity of electric scooter for adults has transformed the urban commuting and recreational landscape. The demand for eco-friendly, efficient, and stylish transportation options has…